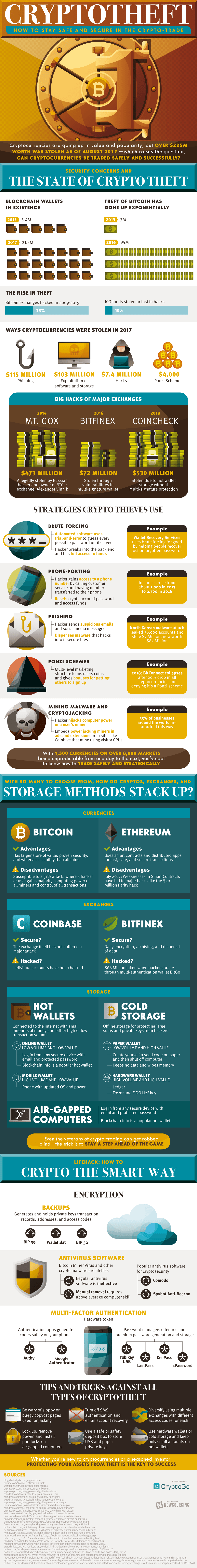
Do you remember back in 2014 when Mt. Gox, which should have never been a cryptocurrency exchange in the first place, got hacked? Russian hackers, thought to be led by Alexander Vinnik, cleaned out $473 million worth of Bitcoin and the site was shut down. People were a little more wary of cryptocurrency then anyway, and it almost spelled the end of the emerging technology. But as with all emerging technologies there are always wrinkles to be ironed out and it takes a lot of hard lessons to find all the wrinkles.
Check out our H2 hedge fund letters here.
The Mt.Gox hack was not the only hack and it wasn’t even the biggest hack - already this year Coincheck has been cleaned out of $530 million in cryptocurrency thanks to hot wallet storage without multi-signature protection. Hackers know these jackpots are ripe for the taking and that the likelihood of anyone being able to find them or even attempting to come after them is slim to none.
Hackers employ a multitude of techniques in order to gain access to your stash of cryptocurrency. Brute-forcing is the method by which hackers employ software to guess every possible password until they gain entry - a method sometimes used to help people gain access to their own accounts when they forget a password. Hackers can also call customer service and give them your phone number and ask them to change the number associated with the account to theirs - a practice known as phone-porting, which allows them to be able to change your passwords. Phishing, Ponzi schemes, malware and cryptojacking are all additional methods of gaining access to your cryptocurrency. It can seem that this is just not a safe investment at all if you don’t know what you are doing.
Fortunately there are way to protect yourself from hackers when investing in cryptocurrency. Knowing the basics is the first step. Different cryptocurrencies have their own advantages and disadvantages, so starting with a cryptocurrency that is more secure is your best bet. Depending on how you plan to use your cryptocurrency you have to choose between a hot wallet, which is easier to use but less secure, and a cold wallet, which is harder to use but significantly more secure. Do you want it to be mobile or completely offline? Depends on how you intend to use it. Air gapped computers allow you to log in from any secure computer, and encryption is crucial to protecting your fortune.
Learn more about protecting your cryptocurrency fortune from this infographic!