The cybercriminal underground has long had its eye on the health care industry. Historically speaking, the financial industry was the primary target, but it didn’t take long for cybercriminals to recognize the goldmine that is the health care industry. There are three key reasons the health care records are a lucrative target:
- Health care records provide detailed data sets for cybercriminals. They contain PII such as SSNs, addresses, phone numbers – which can be used for account takeovers (ATO) – and creating synthetic IDs. Insurance data can be used to create false claims. In addition, medical histories can be used to target VIPs. We have already seen cases where nation states targeted neighboring countries for this type of data. Lastly, health-related information that can be used to purchase drugs.
Q2 hedge fund letters, conference, scoops etc
- Relative to other industries, health care infrastructure is not as secure. Many systems use dated operating systems, and as the case with critical infrastructure, patching and updating is a burden. Access to different platforms and systems is often performed with older browsers. Ransomware attacks have had their fair share of success in this industry as a result of these weaknesses.
- Cybercriminals and threat actor groups have different capabilities and interests. Those individuals and groups who steal data and then sell it (rather than using it themselves) place great value on patient records. While credit cards sell individually for low rates (typically from $1 up to $5), patient data can go for as high as $50.
With a high value, softer attack surface and a variety of attacks and manipulations that can be performed with health care records and data, it only makes sense that cybercriminals target the healthcare industry with great frequency.
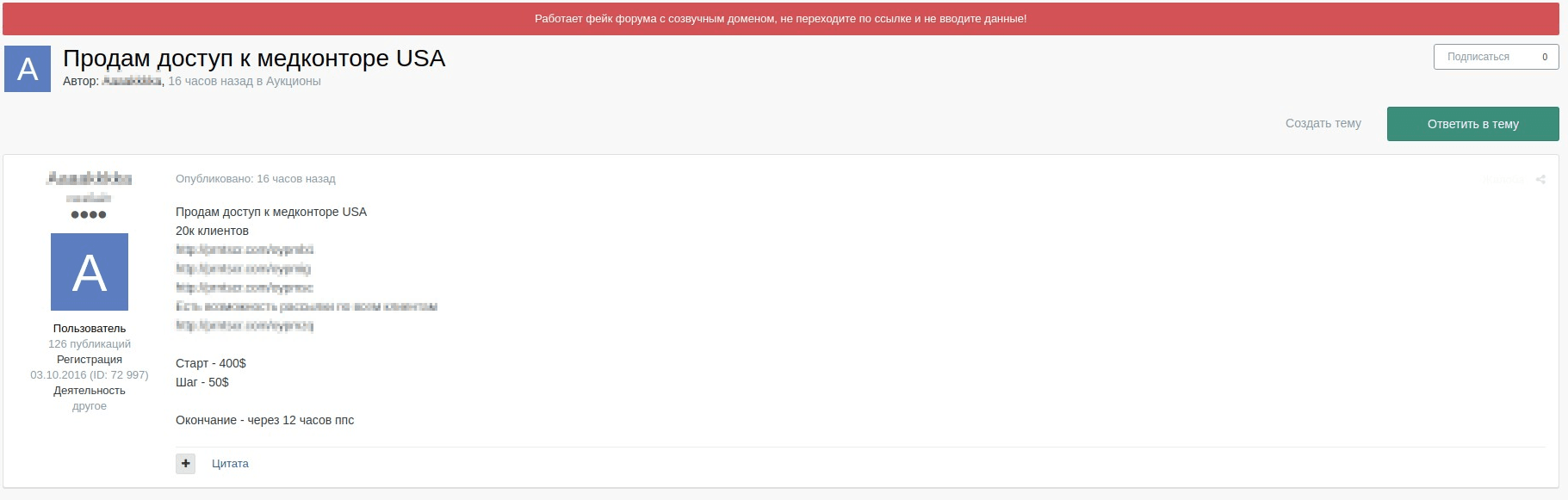
In recent weeks, IntSights researchers have seen an uptick on a special variation of health care data for sale. Rather than selling databases containing patient data or forged insurance cards, cybercriminals are auctioning admin access to health care portals. This type of offering gives the buyer a master key to all data related to the targeted facility. In the example below, the seller is auctioning this type of access with a starting price of $400.
The seller shows access to an administration panel containing various types of sensitive information, including patient data and system users.
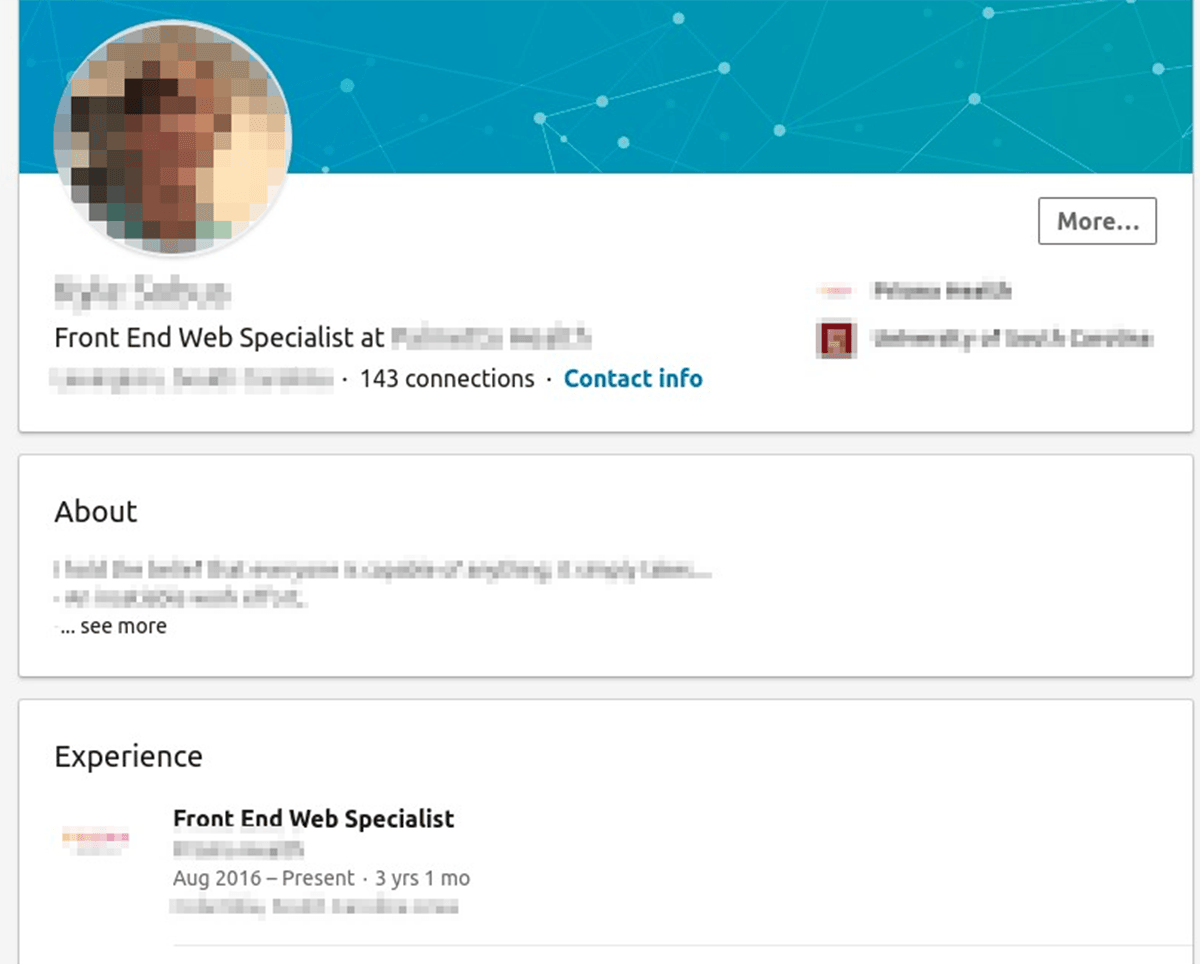
Upon investigation of the related data the seller advertised, IntSights researchers were able to identify the targeted institute, as well as the employee whose credentials were compromised and used to gain backend access.
This is not the only such case – there are offerings like the one below, in which the seller is offering access to a Louisiana internal health care provider with data from over 20 clinics that includes patient and doctor data, as well as infrastructure access.
Administrator access to backend systems is the holy grail for attackers. It provides access to different assets, databases, and information – allowing the attacker to easily steal, alter, or corrupt the data. The ramifications are potentially devastating for those afflicted, from both an organizational and individualistic perspective.
Just like any other industry, health care facilities are always looking for ways to grow and expand their abilities. But expansion inevitably broadens their attack surface even further. Health care organizations are now facing a growing number of attacks and threats while also having to keep in line with different regulatory compliances such as HIPAA. This is why the health care industry is prioritizing and ramping up security protocols – H-ISAC is a great example of the community’s commitment to security – and is now adopting advanced cybersecurity techniques and cyber threat intelligence to help identify and stop these threats as early as possible. Continued investment in and development of sophisticated security initiatives is crucial to protect the extremely sensitive data health care organizations oversee.