Author: Ryan Weeks, Chief Information Security Officer at Datto, Inc.
Over the course of Q1 2018 through Q1 2019, the number of enterprise ransomware attacks skyrocketed by nearly 340 percent, per a report by Malwarebytes. Though the report showed a steep decline in consumer threats (24 percent year over year), ransomware against business targets increased by 195 percent in just one quarter – from Q4 2018 to Q1 2019. According to the Bitdefender “Mid-Year Threat Landscape Report,” ransomware in 2020 will prove a more dangerous threat than ever before.
Though ransomware attacks are not a new phenomenon – the first incident occurred in 1989 – the threat they pose continues to grow. Ransomware is a malicious software that denies access to data or systems until a ransom is paid, usually in the form of cryptocurrency. Prevention is no easy feat, but the best ransomware defense is to have an actionable plan that you never need to use. Since no organization is immune, it’s critical that crisis plans outline the steps needed to mitigate the risk of an attack and/or lessen the severity of attacks that are successful.
The Scary Truth About Ransomware
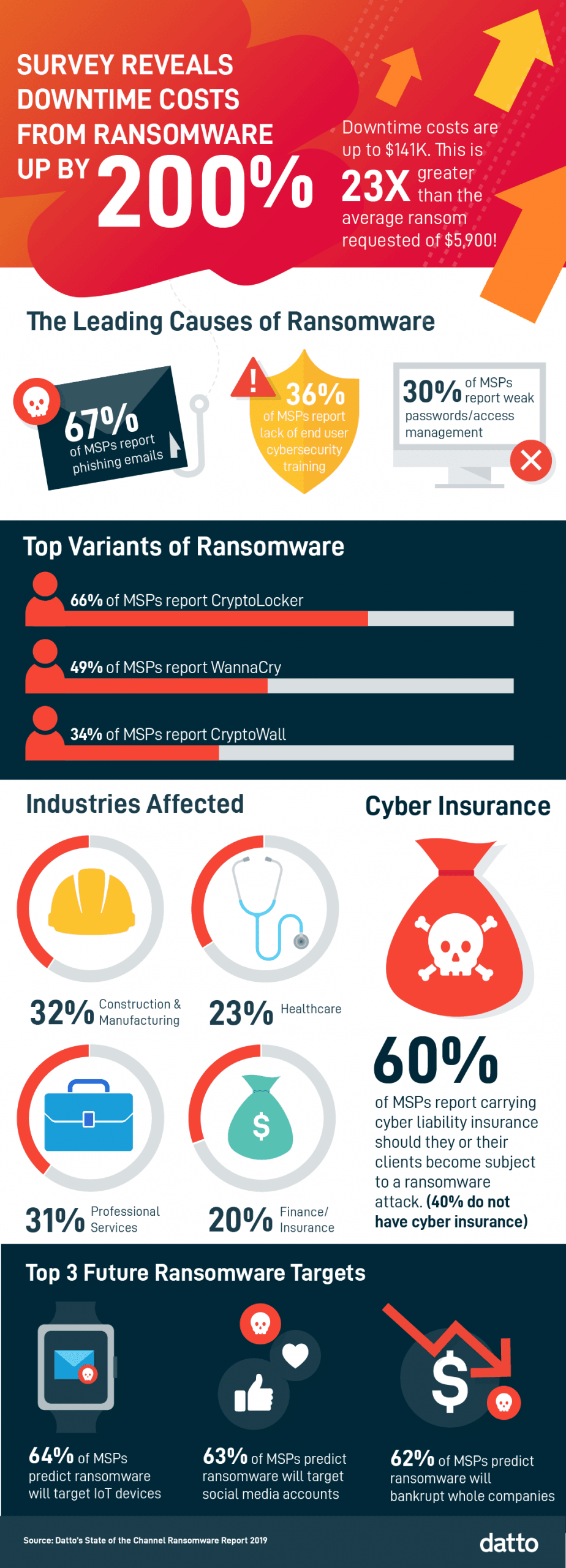
Ransomware has caused significant financial damage across the globe. One of the more damaging results of an attack is the downtime organizations suffer. According to the Datto 2019 Global State of the Channel Ransomware Report, the average cost of downtime due to a ransomware attack is up 200 percent to roughly $141,000. That’s an expensive problem.
The ramifications of a ransomware attack differ based on various specifics, but the consequences are typically interchangeable:
- Loss of business productivity (including dreaded downtime)
- Lost data and/or device
- Infections spread to other devices on the network
- Decreased client profitability
Though ransomware attackers do not discriminate, some industries are hit more often than others. Historically, construction and manufacturing are most vulnerable to ransomware, because these industries are in a constant state of flux and are impacted by the ups and downs of the economy. Because of this, much of their work is project-based and recurring revenue is rare, making it difficult to invest in IT staffing or IT services that require monthly fees. Professional services, healthcare, finance/insurance, non-profits, legal, retail, real-estate, architecture/design, government, and education are also highly vulnerable.
A Look Back at 2019
2019 proved record-breaking for ransomware activity, and the gruesome reality that an experienced hacker needs just seven minutes or less to gain access to a company’s accounting and financial systems after obtaining privileged access credentials, according to Ponemon Institute research.
Once an organization falls victim to a ransomware attack, the FBI encourages victims to refrain from paying the ransom. Paying ransom does not guarantee an organization will regain access to its data and also fuels the fire for future attacks. That being said, paying ransom, in some cases, may be an organization’s only option if they have not taken a proactive approach to recovery planning and threat prevention. Rarely is one able to learn to swim while drowning. Whether or not an organization was just hit by ransomware, or is fortunate enough to have not fallen victim, it is crucial that they implement immutable backups and other defenses to mitigate the risk.
For example, instead of paying ransom, Louisiana Governor John Bel Edwards declared a state of emergency in late November, following a cyberattack on state government servers. Fortunately, the state activated its cybersecurity response team, and did not lose any data or need to pay a ransom. While email and various state websites were shut down for a short period, this was due to the state taking extreme emergency protective measures, including shutting down server traffic to neutralize the attack. These protective actions likely saved the state from data loss and weeks of service outages.
According to the Datto 2019 Global State of the Channel Ransomware Report, traditional cybersecurity solutions like antivirus and email/spam filters are no match for many cyber attackers. Though this report focused on managed service providers’ (MSPs) customer base of small and medium-sized businesses (SMBs), its recommendations are valid across all organizations regardless of size. Recommendations from the report include:
- Organizations need to take a multilayered approach to ransomware, with business continuity at the core.
- The leading causes of ransomware attacks are phishing emails (67 percent), weak passwords/access management (30 percent), and lack of cybersecurity training (26 percent), and therefore organizations should address these areas.
- The majority of ransomware infects endpoint systems (89 percent), clearly calling for companies to reassess their endpoint security strategies.
Ensuring Recovery and Continuity in the Face of Growing Threats
The good news is that it’s not all doom and gloom for those that prepare for the possibility of an attack. Datto’s ransomware report also found that 92 percent of IT service providers report that clients with Business Continuity and Disaster Recovery (BDCR) solutions in place are less likely to experience significant downtime during a ransomware attack, but only about half of SMBs have a disaster recovery plan in place. Those that do are armed to fight the infection, including the ability to reimage a machine, virtualizing the system from a backup image, and running software to cleanup threats, to name a few. Those that choose to take the risk (93 percent) often find themselves out of business after a data breach.
Coming Attractions
As the ransomware epidemic continues and threat actors find new ways to wreak havoc, it is crucial that all organizations take steps to protect themselves. It is no longer a choice – 2020 budgets must be allocated to strengthen overall security posture, which includes:
- Awareness training throughout the organization, regardless of size;
- Improved response time in the face of a threat can mean the difference between success and failure;
- Identification and mitigation of gaps in backup processes, and;
- Practice! Ensure your strategy is flawless by practicing and improve wherever needed.
To keep pace and prepare for a worst-case scenario, it is essential that organizations, ranging from healthcare to construction to entertainment, leverage rock solid ransomware strategies to ensure their data is backed up and recoverable across a rapidly expanding number of locations and IT environments.