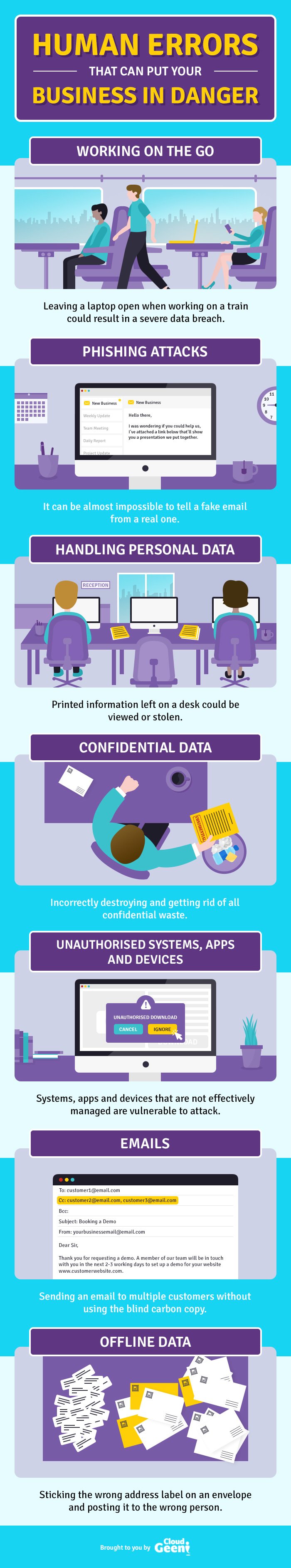
When it comes to online attacks and data hacks, it’s something that is rarely out of the news. As much as we might think that the biggest cause for such attacks are cybercriminals, data released under the Freedom of Information Act reveals that human error is seven times more likely to cause data protection breaches than hackers.
For that reason Cloud Geeni looked at some of the most common every-day risks when it comes to data privacy infringements.
Q2 hedge fund letters, conference, scoops etc
The hosted desktop solutions company has created a visual showcasing example of situations that can put your business in danger when it comes to data protection breaches.
Remote workers
More and more businesses are allowing their staff to work remotely. While this has many positive benefits for both the employers and employees, removing personal and sensitive data from the office does generate additional data security risks.
For example, simply leaving a laptop open when working on a train could result in a severe data breach. According to iPass, remote and mobile workforce is the biggest threat to your business's data security.
To help to prevent data loss or theft, make sure your business has relevant policies and procedures in place. Things like Two Factor Authentication (2FA), adequate password controls, implementing antivirus software, and the ability to quickly remove sensitive data from devices remotely (e.g. via a hosted desktop) can help to reduce the risk.
Phishing attacks
According to research from Mimecast, 94% of organisations have experienced either phishing or spear phishing attacks in the past 12 months. This highlights how important it is to make sure that your employees know how to recognise such scams.
Criminals are getting more sophisticated, and sometimes it’s almost impossible to tell a fake email from a real one. For that reason, make sure you look at how else you can improve your resilience against phishing. For example, by implementing anti-spoofing controls such as DMARC, SPF and DKIM.
Handling personal data
Without relevant security measures in place, it’s easy to see how printed information left on a desk could be viewed or stolen. But that’s not the only way information can be misused, even unattended computers are a threat - because if someone sits at a desk other than their own, they could get access to data that they are not authorised to see. Protect your business from this threat and implement a ‘Clear Desk and Screen’ policy and ensure your employees abide by it.
Confidential data
Another important step is to ensure that personal and sensitive data is correctly disposed of, otherwise, it can fall into the wrong hands. Your organisation should correctly destroy and get rid of all confidential waste (e.g. via a corporate shredding policy and media destruction service).
Unauthorised systems, apps and devices
Systems, apps and devices that are not effectively managed are vulnerable to attack. It’s very important that you establish what devices and applications your employees can use. It’s also essential to ensure your team members are not downloading unauthorised software onto their work devices. This will avoid the risk of malware or ransomware.
Also, where people are using their personal devices to access confidential information, businesses should create a BYOD policy to confirm what devices and applications are allowed to access your network, where and how it can be accessed, and the consequences of breaching the policy.
Emails
According to the Information Commissioner’s Office (ICO), most security breaches happen because of distractions or mistakes. For example, it’s all too easy to send an email to multiple customers without using the blind carbon copy functionality.
If an employee allows the recipients of an email to see each other’s email addresses, your business could face a data breach investigation.
Mistakenly attaching the wrong information to an email, misspelling an email address or sending it to the wrong person are also common data privacy errors. In response, there must be strict policies and procedures in place to ensure the safe processing of information.
Offline data
It’s also offline data we need to be aware of. For example, sticking the wrong address label on an envelope and posting it to the wrong person could also have serious consequences. So, when it comes to data protection, it pays to consider all the different ways you use and share data.