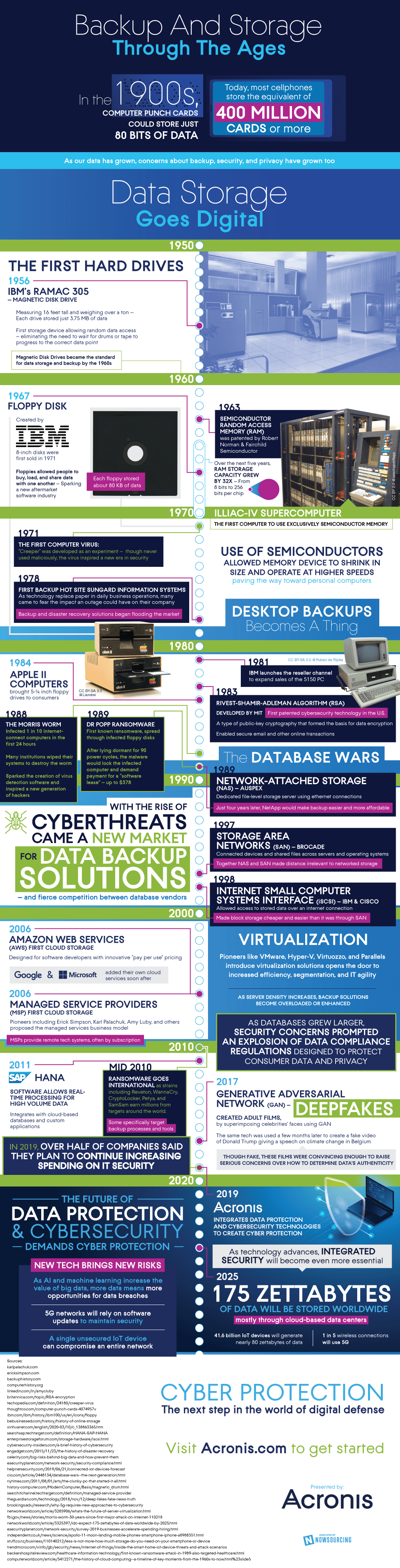
We are finally approaching new heights of memory storage, the next conglomerate of which is the Zettabyte. Excitingly, predictions are that by 2025 we will be storing 175 Zettabytes of data worldwide. Further, 41.6 billion IoT devices will generate 80 Zettabytes of data. This is astonishing considering the first computer punch cards could only store 80 bits of data. With a brand new world of mind-boggling amounts of data and cloud storage, the security of that data will need to follow shortly behind.
Q1 2020 hedge fund letters, conferences and more
The single most important idea you should have learned from history class is “Those who do not know history are doomed to repeat it.” So if you were listening to your soothsaying history teacher you’d know that every time technology leaps ahead, it’s only a matter of time before someone manipulates the advancements for malintent. This makes investing in security a necessity, not for just when a threat is imminent.
The HistoryOf Memory Storage
If you don’t buy that, just take a look at technology over the past approaching century. In 1956, we went from drums and tape for memory to the first magnetic disk drive with IBM’s RAMAC 305. The public started widely using and benefiting from this invention through further advancement via RAM and floppy disks.
A little over 30 years later virulent and widespread attacks on hardware and data were launched. The Morris Worm infected 1 in 10 computers in just 24 hours, causing mass loss of data, and soon after the first ransomware locked down victims’ computers demanding payment for a software license.
In the 1990s databases were becoming more advanced even removing the need to be physically connected to memory via vastly connected servers and networks. This time people knew to prepare, creating a market for data backup solutions. This only answers part of the problem though, while we can’t have data held for ransom since we have a backup, there is data that we don’t want others to have.
Only 20 years later ransomware extorts millions around the world some specifically targeting backup processes and tools. The newest threats have come even more swiftly than in the past, not even 10 years later Generative Adversarial Network (GAN) was being used to make convincingly realistic videos of celebrities in adult films and Trump speaking in Belgium on climate change. These so-called “deepfakes” are raising concerns of data authenticity.
5G And Big Data
Enter 5G networks and big data, our newest additions and one can’t help but ask “how are we going to protect this?” We already know some potential weak points such as overly connected IoT devices and reliance on software updates to maintain security. We already have some promising leads with techniques such as integrated security, let’s take a step ahead of the curveball, shall we?
Learn more about cyber protection here!