Adaptation towards technology is increasing, and software and applications are used everywhere—even places you probably don’t think about. For instance, your car relies on many different types of software. Software is used for banking and other financial services. Of course, it’s also found on your smartphone, TV, smart thermostat, and many other devices. With software being used all around us, software security is a challenge, and it shouldn’t be taken lightly. To avoid security breaches and problems, proper security must be taken into consideration while the software is being developed. Software without proper security is similar to a person walking a high wire without a safety net.
Software Security is a Must as Threats Become More Potent Every Year
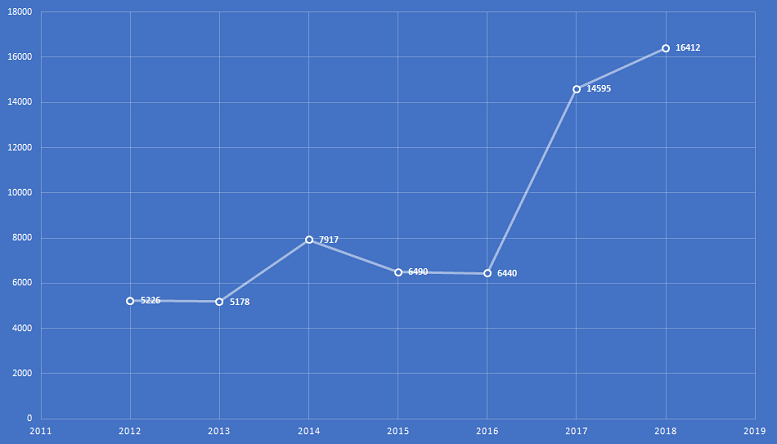
But a lot of the software being released currently falls short of the mark. In fact, vulnerabilities and exploits have increased year by year. For instance the National Vulnerability Database report shows that vulnerabilities in 2018 increased by 12% compared to 2017.
Essential Steps for Software Security
How can you take action to reduce the risk of your software having a significant vulnerability or breach? Here are some common software security steps you can take to improve the security of your software:
Protect Databases From SQL Injection
SQL injection (SQLi) is one of the dangerous attacks, and it has been lingering around for more than a decade. It’s an attack where cybercrooks insert SQL code into a dynamic SQL statement. It’s one of the easiest vulnerabilities for an attacker to find and exploit. Hackers can use free tools such as SQL Ninja or SQL Map to execute an attack. Depending on the database and the attack, the hacker may only be able to read your database information, or they may be able to insert, delete, or update values.
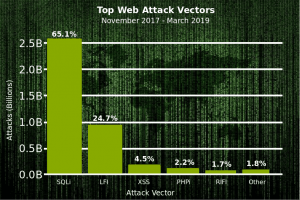
The recent Akamai report noted that “in the first quarter of 2017, SQLi accounted for 44% of application layer attacks. This actually represented a rather large drop from the previous baseline, which was historically slightly over 50%.” SQLi attacks may have dropped slightly, but they’re still one of the largest threats out there.
Recommended Steps to Protect Your Application from an SQL Injection Attack:
- Familiarize yourself with how SQL injection attacks work. Check out some of the many tutorials available on SQL injection to prevent flaws in coding.
- Adopt proper input validation techniques for protecting SQL statements.
- Servers and associated software should be patched and updated.
- Use database logging and backups to detect and respond to any attacks.
- Use application and network penetration testing to find vulnerabilities before attacker do.
- Finally, use a cloud-based web application firewall.
Confirm Input Data Before Using or Storing It
Data coming from outside your service or program must be validated before trusting it. It doesn’t matter whether it has been verified by the client or another system—data must be verified again.
Basic rules to practice for the validation of data:
- Always check the data on the server, rather than relying on client-side code.
- Make use of strong whitelist rules. Specify the range and size of acceptable values.
- Refer to libraries such as Apache Commons Validator. Check data types such as currencies, IP addresses, dates, and other sensitive details like credit card numbers.
Implement Proper Access Rights
First, you need to decide who must be given what rights—for example, what types of data and features of the software they can access. Next, you’ll need to decide how rules will be enforced. Then you’ll need to carefully implement these rules: it’s time-consuming and frustrating to redo work on access control once the development process is completed.
Here are some basic rules of software security you should follow:
- For providing access rights, use data that is trusted by the server. (Data that has been validated).
- All software functionalities must check the authorization of the user before proceeding further.
- Access rights must be implemented in a server-side library.
- Access should be granted at a very specific level, to ensure that users don’t have more access than they need.
Establish Bulletproof Authentication
Some hackers simply login to an application by sneaking through your authentication system. Here are some tips to avoid this:
- Try to use multi-factor authentication.
- Enforce a mandatory length and complexity for passwords.
- Make use of salting & hashing for password storage.
- For password recovery, design a secure recovery function that verifies security answers before proceeding.
Sign Your Software and Applications
Even if your software is well developed and fully secured, it will not be trusted by users if it shows a warning message. Sign your software with a code signing certificate offered by a trusted certificate authority such as Sectigo. This helps users avoid unwanted warning signs. On the other side, if any malicious actor has tried to infiltrate it with malware a warning will be shown to the user. This protects your users and your brand reputation.
Logging Timestamps and Intrusion Detection
Logging is important for many reasons. It helps in troubleshooting, debugging, and for auditing critical activity and intrusion detection.
- Consider which information you need to log carefully before implementing your logging strategy. What information should you store? For example, the user ID, address information, source IP, and event details.
- Follow the same logging approach throughout the development process. This makes correlation and analysis easier.
- Use an extensible logging framework such as Apache Log4j/Log4j2 or SLF4J with Logback. Review your logging practices and test whether they are working correctly and securely.
- Encode user data before logging to protect against hackers getting sensitive data from your log files.
Handle Exceptions and Errors Properly
Handling Errors isn’t easy. One single mistake in handling errors and exceptions can lead to many types of problems as well as serious security vulnerabilities.
For example, detailed error messages can reveal the architecture of your software. This type of information can be very helpful to an attacker who’s trying to penetrate the system. Another famous example is displaying an “invalid password” or “invalid user” message rather than an “invalid logon.” This can be helpful to users, but it’s a big help to attackers.
Automated Security Testing
With agile software releases are often pushed out at an amazingly fast rate. This means it’s not always possible for penetration testers and security auditors to keep up with it. That’s why it’s important to include automated security checks as part of your continuous delivery and continuous integration pipeline.
Wrapping Up Software Security Tips
So here you have it: 8 software security tips you can follow while developing software. If we’ve missed something or you have something to add, let us know in the comments section below!