A security researcher tried to contact Careem a major ridesharing app in emerging markets, about a potential big data issue, but the company did not take it seriously, argues the security expert in a major expose posted earlier today.
Careem App is a car booking platform based in UAE which offers traveling services by which people can book a car on their doorstep in a couple of minutes. Careem App is known for its pick and drop service with the most comfortable and safe environment all over UAE, PAKISTAN, AFRICA and more countries. But, what if this multinational organization gets comprise by hackers and their billion dollars worth customer’s data gets leak. They’d have nothing to do except regretting.
Few weeks ago, a InformationSecurity Researcher named Daniyal Nasir from Karachi, Pakistan diged into the Careem Applications to test for the security issues and found the most critical vulnerabilities in their applications by which he was able to access over 1.4 million customer’s confidential information of Careem.
Daniyal Nasir is an Independent Application Security Researcher and Bug Bounty Hunter at HackerOne, and Currently Serving as a Security Analyst and Forensics Investigator in a Private Company in UAE. He has been Acknowledged by over a hundred of Reputed Organizations including Microsoft, Sony, SalesForce, Intel, SAP,Buzzfeed, Github, Starbucks etc for reporting major security flaws in their applications.
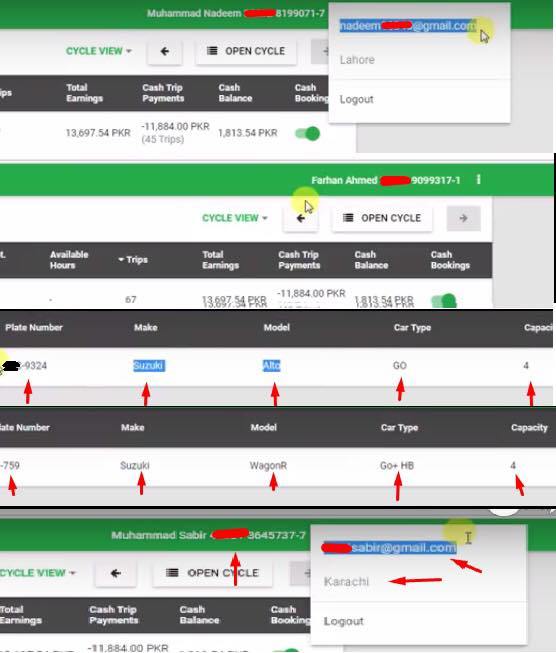
He was able to get all the Information of Careem includes all the Driver’s Email, Name, Mobile Number, ID CardNumber, Trips, Payment Information, even their Pictures. Not only drivers, but also the details of all the Cars registered in Careem even their Car Registration Number.
We can’t disclose the affected domains and any type of private information due to some security reasons.
Daniyal Nasir with Securitywall tried to reach the Careem appropriate team to discuss about these vulnerabilities but no positive response was coming from their side. In short, they were not interested to hear this kind of news, which was very important for them.
He tried to contact to their local MD and CEO Mudassir Sheika, also their members of technical departments and support teams. But, same as before there was no positive response and replies were getting delayed about main issues we were offering to discuss.
Careems Reply to the Researcher
These kind of auto reply hurt companies where reporters like “Daniyal Nasir” tends to secure application and customer services have this kind of mails to respond. In past Securitywall team did report to zameen.com, pakwheels, where they replied with such auto responding messages and after months they get through same parameters which we reported.
These are some Screenshots which was taken by Daniyal Nasir as the Proof-of-Concept of the Vulnerability. As you can see that all the data of the Drivers can be clearly shown.
After waiting a lot of time for a positive response, we realized that they’re not having interest to improve their application’s security nor interested to save Careem from a big data breach. We left them as it is.
After some days, Researcher noticed that the low hanging issues has been fixed by Careem without even knowing to us which was sad, but still many vulnerabilities was present at that time which could be harmful for their business and also a huge loss of their customers, drivers, vendors. Two Days ago we contact them again with detail and Careem agreed on launching a bug bounty program to involve security reporters, but we don’t have any clue when it will get started and where reporters can report, Hopefully we can push an update here.
This Post is just to aware brands and developers to make sure to pen-test your applications while some bad guys can come in and hurt you in many ways, our job was to notify and report which we did to Careem, and this was not our first time to report critical issues. We have reported many vulnerabilities in top reputed brands and organizations where they have appreciated our ethical approach and now are into pentesting their apps. A good approach ins’t it?
We hope local brands will learn something productive from here…